Last month’s ITEX 365 newsletter discussed the importance of a business impact analysis (BIA) when conducting disaster recovery and business continuity planning, concentrating on Recovery Point Objective (RPO) and Recovery Time Objective (RTO). This article dives deeper to determine how these variables impact loss due to a cybersecurity breech.
How long can your business be without service before you incur substantial loss?
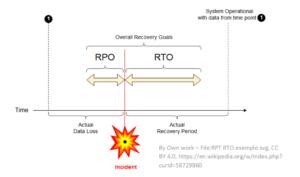
RTO (Recovery Time Objective) can be defined as the start of the interruption and time to establish recovery and end when you can successfully release the service back to your users. The goal is to calculate how quickly you need to recover and then to map out the people, processes, and budget allotment you will need towards business continuity.
RPO (Recover Point Objective) often refers to the last available restore backup and the maximum time between backups being safely stored offsite. This focus is on your data and your company loss tolerance—how long can you afford to operate without your data before your business suffers.
Have you ever had a computer crash or lose power while you are in the middle of a huge spreadsheet with lots of data entry, calculations, and detailed graphs? How much time and effort would it require for you to try to recover the spreadsheet from your last save, or what happens if you can’t recover and need to start over from scratch? It’s simply painful. Multiply that pain by every person, device, and data point in your organization.
Both RTO and RPO influence the type of redundancy and backup infrastructure you need to have in place. Besides time and money, you will need to consider compliance and your trust reputation with your clients. At what point would you begin to lose customers? Another factor to consider is your RTA (Recovery Time Actual) or the actual performance of your disaster recovery/business continuity plan. After planning and implementation, your DR/BC requires continued testing to validate success. If there is significate gap between your goal (RTO) and your actual results (RTA), you’ll want to rethink your strategy to improve the time it takes to restore and become operational again.
Business Impact Analysis
Key takeaways from the business impact analysis should detail a listing of your critical systems and processes ranked by priority. This list should include 3rd party vendor software, cloud software usage, on premise software, on premise hardware that affects day-to-day operations (phone systems, devices used by employees, fax machines), IT infrastructure, and even access and security to your property. As you walk through each system, you will record these items:
• Potential impact scenarios
• Dependencies
• RTO
• RPO including actual back up times
• Likely impact
• Potential loss
Ranking all of your systems and infrastructure by priority will give you a clear map of what needs to be recovered first and what can possibly wait. Identify the manual process and the automated processes as well and include vendor contact information for assistance on each of these systems.
If you are subject to compliance regulations, protecting your data isn’t optional, it is a legal obligation. Disasters happen, cyber warfare is real, and the best resolution is to detail and plan, assign priority duties and communication paths, practice, and budget accordingly.


Leave A Comment
You must be logged in to post a comment.